A customer ask me if the PAN could automatically block an IP address if it triggers a threat log. At first I started to think that I could do it through an EDL and use Elastic Stack, but then I remembered the built-in actions on a log forwarding profile – that’s way easier.
I decided to take a look to see what filter I could use to choose the source IPs. I landed on this because I had some TCP fast opens from 1.1.1.1 on odd ports, and I don’t want to start blocking 1.1.1.1.
zone.src eq Outside and !(severity eq informational and app eq not-applicable)Next we go add this to the logging profile and add a new match list and built-in action to add a tag to the source ip that times out after how ever long we want to put the IP in timeout.

Then we create the dynamic group for it

Then we add that group to the block rules we probably already have

I waited about an hour and I had my my first hit

if you don’t have that much patience, you can also test it out
debug object registered-ip test register tag AutoBlock ip 192.0.2.1
clear auto-tag ip 192.0.2.1 tag-dest AutoBlock registration localhost tags AutoBlockYou can look back at the history of the blocking by searching traffic logs for the AutoBlock rule and you can history of tagging by looking at logging:
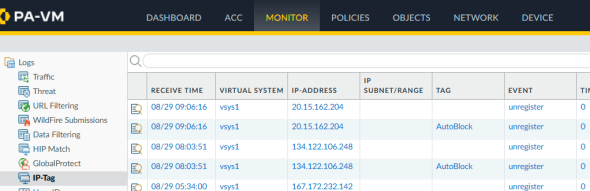
or use the CLI command
show log iptag
Very cool Steve! I got to try this out!